Its next generation firewalls enable unprecedented visibility and granular policy control of applications and content by user not just ip address at up to 10gbps with no performance degradation.
Palo alto firewall cheat sheet pdf.
Key features performance capacities and specifications for all palo alto networks firewalls.
However since i am almost always using the gui this quick reference only lists commands that are useful for the console while not present in the gui.
Maybe some other network professionals will find it useful.
Based on patent pending app id technology palo alto networks firewalls accurately.
Therefore i list a few commands for the palo alto networks firewalls to have a short reference cheat sheet for myself.
You must have superuser superuser read only device administrator or device administrator read only access to use these commands.
Palo alto networks is the network security company.
Change the arp cache timeout setting from the default of 1800 seconds.
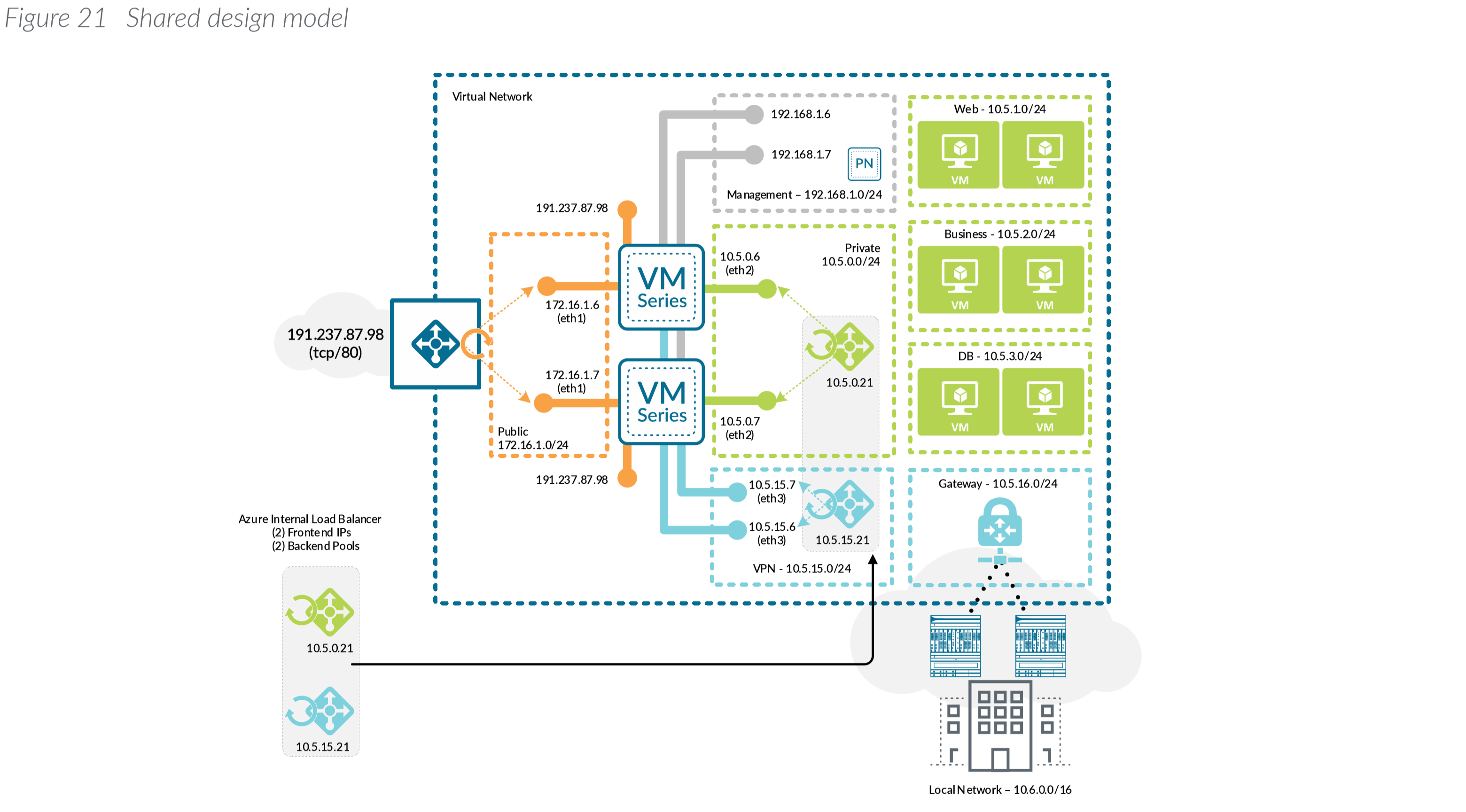
Creating and managing security policies based on the application and the identity of the user regardless of device or location is a more effective means of protecting your network than relying solely on.
Now that you know how to find a command and get help on command syntax you are ready to start using the cli to manage your palo alto networks firewalls or panorama the following topics describe how to use the cli to view information about the device and how to modify the configuration of the device.
Vsys use the following commands to administer a palo alto networks firewall with multiple virtual system multi vsys capability.
Vsys use the following commands to administer a palo alto networks firewall with multiple virtual system multi vsys capability.
Show user server monitor state all view how many log messages came in from syslog.
User id view all user id agents configured to send user mappings to the palo alto networks device.
Palo alto networks pa 800 series next generation firewall appliances comprised of the pa 820 and pa 850 are designed to secure enterprise branch offices and midsized businesses.
To see all configured windows based agents.
You must have superuser superuser read only device administrator or device administrator read only access to use these commands.